Cisco 210-260日本語 : Implementing Cisco Network Security (210-260日本語版)

- Exam Code: 210-260日本語
- Exam Name: Implementing Cisco Network Security (210-260日本語版)
- Updated: Aug 31, 2025
- Q & A: 515 Questions and Answers
About Cisco 210-260日本語 Exam
Who should take the 210-260 Exam
The certification is fashioned for:
- Network security engineer
- Network security administrator
- Network security analyst
- Network support engineer
- Senior network engineer
- Network security specialist
When it comes to 210-260日本語 certification, all of us are very excited and have a lot words. Someone complains the difficulty of the actual test, someone says he has get stuck in one questions, even some people are confused about all of the 210-260日本語 exam test. Actually, gaining the 210-260日本語 certification can bring about considerable benefits. For example, having the 210-260日本語 certification on your resume will give you additional credibility with employers and consulting clients, and a high salary & good personal reputation will come along with that. From the above, we can see how important the 210-260日本語 certification is. Our life is deeply affected by the IT technology and 210-260日本語 certification.
Now, we will recommend the most valid & best-related 210-260日本語 exam study torrent for your preparation. No matter how much you are qualified or experienced, we are just here to assist you pass the 210-260日本語 test with 100% results.
For more info visit
Cisco 210-260 Exam Topics:
| Section | Weight | Objectives |
|---|---|---|
| VPN | 17% | 1 VPN concepts a) Describe IPsec protocols and delivery modes (IKE, ESP, AH, tunnel mode, transport mode) b) Describe hairpinning, split tunneling, always-on, NAT traversal 2 Remote access VPN a) Implement basic clientless SSL VPN using ASDM b) Verify clientless connection c) Implement basic AnyConnect SSL VPN using ASDM d) Verify AnyConnect connection e) Identify endpoint posture assessment 3 Site-to-site VPN a) Implement an IPsec site-to-site VPN with pre-shared key authentication on Cisco routers and ASA firewalls b) Verify an IPsec site-to-site VPN |
| Secure Access | 14% | 1 Secure management a) Compare in-band and out-of band b) Configure secure network management c) Configure and verify secure access through SNMP v3 using an ACL d) Configure and verify security for NTP e) Use SCP for file transfer 2 AAA concepts a) Describe RADIUS and TACACS+ technologies b) Configure administrative access on a Cisco router using TACACS+ c) Verify connectivity on a Cisco router to a TACACS+ server d) Explain the integration of Active Directory with AAA e) Describe authentication and authorization using ACS and ISE 3 802.1X authentication a) Identify the functions 802.1X components 4 BYOD a) Describe the BYOD architecture framework b) Describe the function of mobile device management (MDM) |
| IPS | 9% | 1 Describe IPS deployment considerations a) Network-based IPS vs. host-based IPS b) Modes of deployment (inline, promiscuous - SPAN, tap) c) Placement (positioning of the IPS within the network) d) False positives, false negatives, true positives, true negatives 2 Describe IPS technologies a) Rules/signatures b) Detection/signature engines c) Trigger actions/responses (drop, reset, block, alert, monitor/log, shun) d) Blacklist (static and dynamic) |
| Content and Endpoint Security | 12% | 1 Describe mitigation technology for email-based threats a) SPAM filtering, anti-malware filtering, DLP, blacklisting, email encryption 2 Describe mitigation technology for web-based threats a) Local and cloud-based web proxies b) Blacklisting, URL filtering, malware scanning, URL categorization, web application filtering, TLS/SSL decryption 3 Describe mitigation technology for endpoint threats a) Anti-virus/anti-malware b) Personal firewall/HIPS c) Hardware/software encryption of local data |
| Secure Routing and Switching | 18% | 1 Security on Cisco routers a) Configure multiple privilege levels b) Configure Cisco IOS role-based CLI access c) Implement Cisco IOS resilient configuration 2 Securing routing protocols a) Implement routing update authentication on OSPF 3 Securing the control plane a) Explain the function of control plane policing 4 Common Layer 2 attacks a) Describe STP attacks b) Describe ARP spoofing c) Describe MAC spoofing d) Describe CAM table (MAC address table) overflows e) Describe CDP/LLDP reconnaissance f) Describe VLAN hopping g) Describe DHCP spoofing 5 Mitigation procedures a) Implement DHCP snooping b) Implement Dynamic ARP Inspection c) Implement port security d) Describe BPDU guard, root guard, loop guard e) Verify mitigation procedures 6 VLAN security a) Describe the security implications of a PVLAN b) Describe the security implications of a native VLAN |
| Cisco Firewall Technologies | 18% | 1 Describe operational strengths and weaknesses of the different firewall technologies a) Proxy firewalls b) Application firewall c) Personal firewall 2 Compare stateful vs. stateless firewalls a) Operations b) Function of the state table 3 Implement NAT on Cisco ASA 9.x a) Static b) Dynamic c) PAT d) Policy NAT e) Verify NAT operations 4 Implement zone-based firewall a) Zone to zone b) Self zone 5 Firewall features on the Cisco Adaptive Security Appliance (ASA) 9.x a) Configure ASA access management b) Configure security access policies c) Configure Cisco ASA interface security levels d) Configure default Cisco Modular Policy Framework (MPF) e) Describe modes of deployment (routed firewall, transparent firewall) f) Describe methods of implementing high availability g) Describe security contexts h) Describe firewall services |
| Security Concepts | 12% | 1 Common security principles a) Describe confidentiality, integrity, availability (CIA) b) Describe SIEM technology c) Identify common security terms d) Identify common network security zones 2 Common security threats a) Identify common network attacks b) Describe social engineering c) Identify malware d) Classify the vectors of data loss/exfiltration 3 Cryptography concepts a) Describe key exchange b) Describe hash algorithm c) Compare and contrast symmetric and asymmetric encryption d) Describe digital signatures, certificates, and PKI 4 Describe network topologies a) Campus area network (CAN) b) Cloud, wide area network (WAN) c) Data center d) Small office/home office (SOHO) e) Network security for a virtual environment |
Valid practice torrent for better study
First, we have built a strong and professional team devoting to the research of 210-260日本語 valid practice torrent. The experts of the team are all with rich hands-on IT experience and ever work for the international IT corporations. The authority and validity of Cisco 210-260日本語 training torrent are the guarantee for all the IT candidates. Maybe, you ever heard that some vendors offer the cheap dumps with lots of useless questions & answers, you have to study really hard with extra number of worthless questions and even they can't promise you success in the exam. Here, 210-260日本語 valid exam torrent will provide you with the best suitable dumps for you to study. Each questions & answers from CCNA Security 210-260日本語 exam study torrent are all refined and summarized from a large number of technical knowledge, chosen after analysis of lots of datum. We remove the old and useless questions which are no longer needed for the actual test, and add the latest question into the Cisco 210-260日本語 exam dumps torrent at the same time. So the high-quality and best validity of 210-260日本語 training torrent can definitely contribute to your success.
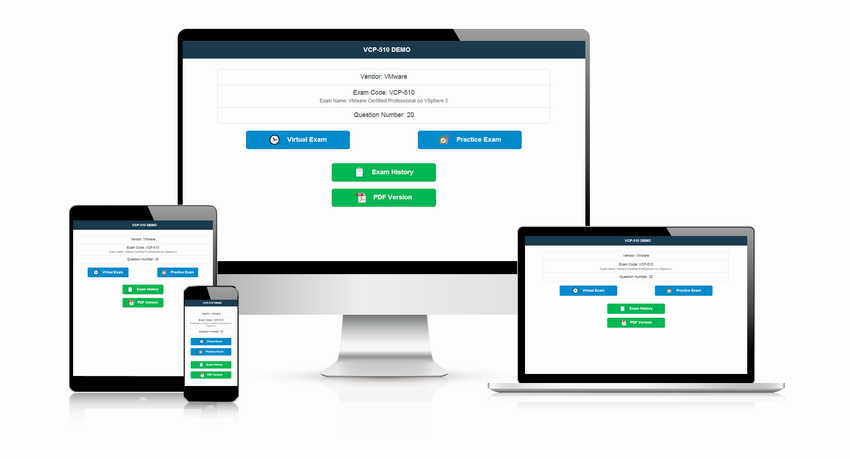
What's more, our specially designed products like 210-260日本語 free demo will provide the customer with the overview about our 210-260日本語 dump torrent. We exclusively offer instant download 210-260日本語 free sample questions & answers which can give right guidance for the candidates.
Safe investment-money back guarantee in case of failure
We commit that you will enjoy one year free update for CCNA Security 210-260日本語 exam dumps torrent after you purchase. That is to say you will grasp the latest information without spending extra money. If there is any update, our system will send an email attached with updated 210-260日本語 exam training torrent to you automatically. In the unlikely even if you fail the 210-260日本語 exam, we promise to give you full refund. The refund policy is very easy to carry out, you just need to send us an email attached with your scanned failure certification, then we will give you refund after confirming. We will refund your money to the same card that is used to make payment. Besides, if you have any questions, our 24/7 Customer Support are available for you.
Choose our 210-260日本語 Implementing Cisco Network Security (210-260日本語版) valid practice torrent, we guarantee you 100% passing.
Instant Download: Upon successful payment, Our systems will automatically send the product you have purchased to your mailbox by email. (If not received within 12 hours, please contact us. Note: don't forget to check your spam.)
Cisco 210-260 Exam Certification Details:
| Duration | 90 minutes |
| Exam Code | 210-260 IINS |
| Exam Price | $300 USD |
| Number of Questions | 60-70 |
| Passing Score | Variable (750-850 / 1000 Approx.) |
| Exam Name | Implementing Cisco Network Security |
| Sample Questions | Cisco 210-260 Sample Questions |
| Exam Registration | PEARSON VUE |
| Recommended Training | Implementing Cisco Network Security (IINS) Implementing Cisco Network Security (IINS) E-Learning |
Related Exam
Related Certifications
Over 79617+ Satisfied Customers
 0 Customer ReviewsCustomers Feedback (* Some similar or old comments have been hidden.)
0 Customer ReviewsCustomers Feedback (* Some similar or old comments have been hidden.)
Quality and Value
Free4Torrent Practice Exams are written to the highest standards of technical accuracy, using only certified subject matter experts and published authors for development - no all study materials.
Tested and Approved
We are committed to the process of vendor and third party approvals. We believe professionals and executives alike deserve the confidence of quality coverage these authorizations provide.
Easy to Pass
If you prepare for the exams using our Free4Torrent testing engine, It is easy to succeed for all certifications in the first attempt. You don't have to deal with all dumps or any free torrent / rapidshare all stuff.
Try Before Buy
Free4Torrent offers free demo of each product. You can check out the interface, question quality and usability of our practice exams before you decide to buy.